Thursday, February 11, 2010
MSExchangeIS Automatic Start When Migrating from SBS2003 to SBS2008
The cause of the issue is that Exchange services depend on following Windows Services:
Event Log
NT LM Security Support Provider
Remote Procedure Call (RPC)
Server
Workstation
When any of these service do not start before Exchange tries to start Exchange services, the Exchange Information Store service cannot be started. You can either change the service dependencies, or you can add BootPause registry key to delay the startup of Exchange Server. Microsoft provides instructions to perform these steps in the following knowledge base article: http://support.microsoft.com/kb/940845/en-us.
Wednesday, February 3, 2010
Free Virtualization Event: Virtualization Untangled - March 18th, 2010
RoseBud Presents - Virtualization Untangled - Join us for this free event - Earn CPE Credit
March 18th, 2010 11:30-1:00p.m.. Held at the offices of Bennett-Thrasher in Atlanta.
Virtualization is unquestionably one of the hottest trends in information technology today. This is no accident. While a variety of technologies fall under the virtualization umbrella, all of them are changing the IT world in significant ways.
This overview introduces Microsoft’s virtualization technologies, focusing on three areas: hardware virtualization, presentation virtualization, and application virtualization. Since every technology, virtual or otherwise, must be effectively managed, this discussion also looks at Microsoft’s management products for a virtual world. The goal is to make clear what these offerings do, describe a bit about how they do it, and show how they work together.
Free Windows 7 shirt for all who register.
Register here: https://support.rosebudtech.com/events/
Thursday, January 28, 2010
Technology Roller Coaster
On day where I’m still recovering from a long day, long night, and an early morning support call with Microsoft – I needed a fun reminder as to how neat this technology can be.
Working with a client this morning, we wanted to test our System Center Virtual Machine Manager installation.
On the technical side of the equation, this environment is a three node Windows 2008 R2 Hyper V failover cluster connected to a backend SAN. A separate Windows 2008 R2 server is acting as the virtual machine management console.
We took turns, one by one, putting the virtual host machines into Maintenance Mode. This automatically moves any virtual machines on that particular host another host in the cluster. This move is “live”, so end users don’t know anything is happening while the move takes place or that the server their using is now running from a different virtual host machine.
While the machine is in maintenance mode, we installed Windows Updates and rebooted. Once the reboot was complete, we stopped maintenance mode on the virtual host machine. System Center Virtual Machine Manager then reallocates the virtual machines running on the other virtual hosts back to the reinstated virtual host.
Sometimes technology is just cool.
Friday, January 22, 2010
Establish a VPN connection pre-logon in Vista/Server 2008/Windows 7

- Press CTRL+ALT+DELETE.
- Windows displays the logon screen for the user that last logged on. Press ESC or click Switch User to view other logon choices.
- A blue button appears to the left of the red Shutdown button. Click the blue button. Windows displays a list of system-owned dial-up connections for you to choose, if there is more than one. Otherwise, Windows uses the single system-owned connection.
- If prompted, type the user name and password for the dial-up connection and click the round blue button to connect.
- Windows then establishes a connection to the remote network using the provided credentials. It uses these same credentials when logging on to the domain.

Thursday, January 21, 2010
Microsoft to Issue Emergency IE Patch Today 1.21.10
Thu, January 21, 2010 — Computerworld — Microsoft will release its emergency patch for Internet Explorer (IE) on Thursday, the company said today as it also admitted that attacks can be hidden inside rigged Office documents.
The Patch Tuesday Survival Guide
"We are planning to release the update as close to 10:00 a.m. PST as possible," Jerry Bryant, a program manager with the IE group, said in an entry on the Microsoft Security Response Center (MSRC) blog.
Yesterday, Microsoft confirmed speculation that it would issue an "out-of-band" update for the IE vulnerability, but postponed specifying a ship date until today.
Microsoft also updated the security advisory it originally published last week when it acknowledged a zero-day IE vulnerability had been used by hackers to break into the corporate networks of Google and other major Western companies. Google has alleged that the attacks were launched by Chinese attackers. Subsequently, security experts have offered evidence that links the attacks to China .
The revised advisory also addressed claims made by researchers that it's possible to exploit the newer IE7 and IE8 browsers, and even circumvent Microsoft's recommended defensive measure, DEP (data execution prevention). However, the advisory waffled on whether DEP bypass was effective, neither confirming or denying the researchers' allegations.
"There is a report of a new Data Execution Prevention (DEP) exploit," Microsoft said in the advisory. "We have analyzed the proof-of-concept exploit code and have found that Windows Vista and later versions of Windows offer more effective protections in blocking the exploit due to Address Space Layout Randomization (ASLR)."
Even a follow-up post by Jonathan Ness, an MSRC engineer, on the company's Security Research & Defense blog declined to spell out whether the DEP bypass attacks were effective. Ness, however, did reiterate Microsoft's point that the only in-the-wild attacks seen thus far have been aimed at IE6.
He also touted the additional security that ASLR and IE's Protected Mode provide, and published a table that spelled out the current attack and threat situation for IE and Windows users.
Microsoft also admitted that the vulnerability could be exploited through malicious Office documents, a vector that had not been disclosed previously. "We are also aware that the vulnerability can be exploited by including an ActiveX control in a Microsoft Access, Word, Excel, or PowerPoint file," said Bryant. "To prevent exploitation, we recommend that customers disable ActiveX Controls in Microsoft Office."
Tomorrow's update for IE will patch all attack avenues, Bryant added, including the Office document vector.
The IE vulnerability has gained considerable attention because it has been connected to the attacks that broke into Google's corporate network. McAfee was the first to reveal that the attacks against Google had been conducted using exploits of the IE vulnerability.
To read the complete article:
http://www.cio.com/article/520729/Microsoft_to_Issue_Emergency_IE_Patch_Thursday?source=rss_news
Tuesday, January 19, 2010
Dell iDRAC6 Enterprise
This is a terrific little gem for remote administration of a server. The iDRAC, integrated Dell Remote Access Controller, allows you to view the remote server during a full reboot, in addition to remote console view, like an RDP session.

The image above is a snapshot of my server booting up.
The card is self-contained so even if the server blue screens, you can still view the machine.
I don’t know if I’d configure this through a publically accessible connection, but I’m certain to configure for the LAN where I could VPN to the network and then launch the browser based iDRAC utility.
As we enter 2010, this card is a must for all server quotes and installations.
Resources:
Tuesday, December 15, 2009
Error When Viewing Roles in Server 2008 Server Manager
Today, I was checking on some things in our virtual server host environment when one of the servers displayed the following when clicking on the “Roles” module in Server Manager.
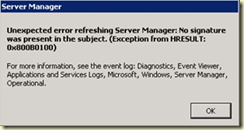
“No signature was present in the subject. (Exception from HRESULT: 0x800B0100)”
This was not a happy thing to find as the virtual host in question is a production server with virtual machines running. The last thing I wanted to do in the middle of the day was to reboot this server.
As the error message suggests, I looked in an area of the Server 2008 Event Logs that I’ve never been before. This event log gets noted as “Microsoft-Windows-ServerManager/Operational”. The error event ID I had in this log was 1601.
A little BING-ing and I happened upon the following article - http://dwjack.spaces.live.com/blog/cns!3EE7D7517C0BC5AE!250.entry. This provides a great run down of the steps involved to resolve this issue. To my surprise, the result of this did NOT require a reboot of the server to implement the changes.
However, I found that the documentation here was a little thin in just the right place. Part of the solution for this “no signature” error is to copy the missing files from a Windows Update into the C:\windows\servicing\Packages directory. The way to do that is to take ownership of the Packages folder and add yourself with full control. However, the initial owner of the folder is TrustedInstaller.
Microsoft Starting with Windows Vista and Server 2008 Windows incorporates Mandatory Integrity Control, which adds Integrity Levels (IL) to processes running in a login session. MIC restricts the access permissions of applications that are running under the same user account and which may be less trustworthy. Five integrity levels are defined: Low, Medium, High, System, and Trusted Installer.
From WikiPedia
When I went back to add TrustedInstaller as the owner, I was not able to find the account. Turns out that the account is an NT SERVICE. I followed the steps in this article to restore ownership to correct account, http://www.vistax64.com/tutorials/159360-trustedinstaller-restore-owner.html. When specifying the account, be sure to change the “Locations…” to the local machine.


 Follow us on
Follow us on  Follow us on
Follow us on  Follow us on
Follow us on